M1 Explain the Operation of Different Intruder Detection Systems
They have different attack methods in their knowledge if something in the network or on the host matches one of these an alarm will be triggered. M1 - Explain the Operation of different intruder detection systems.
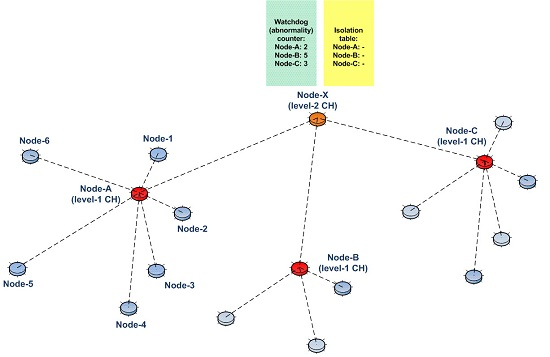
Sensors Free Full Text An Intrusion Detection System Based On Multi Level Clustering For Hierarchical Wireless Sensor Networks Html
M1 - Explain the Operation of different intruder detection systems A Firewall is a software or hardware-based network security system that controlsmonitors the incoming and ooutgoing network traffic by analizing the data packets and determing wehther they should be allowed through or not based on an applied rule set.
. NIDS systems monitor all of the traffic that. Devices eg firewalls virus protection spyware protection file monitoring folder monitoring use of honeypots alarms 3 Understand organisational aspects of network security Policies and procedures. Knowledge Based and Behaviour Based IDS.
The biggest advantage of this is. M1 explain the operation of different intruder detection systems Firewall A firewall can be hardware and software or a router It restricts unauthorized access into or out of networks They are frequently used to prevent unauthorized access into. M1 explain the operation of different intruder detection systems Firewall A firewall can be hardware and software or a router It restricts unauthorized access into or out of networks They are frequently used to prevent unauthorized access into.
They have different attack methods in their knowledge if something in the network or on the host matches one of these an alarm will be triggered. Intrusion detection is the process of monitoring the events occurring in your network and analyzing them for signs of possible incidents violations or imminent threats to your security policies. Explain the operation of different intrusion detection systems M1NIDS - Intrusion detection systems are important if you want to keep your network secure.
Explain the operation of different intruder detection systems. That it has a very low false alarm rate. Bias Busters Prezi Video.
M1 Explain the operation of different intruder detection systems Active and Passive IDS. Backup and recovery schemes. Intrusion Detection System IDS Intrusion Detection System is used to detect unauthorised entries and alert the administrator to respond.
You can implement a firewall in both hardware and software or a combination of both. You can implement a firewall in both hardware and software. It will send an alert to the administrator to let them know what is happening but passive.
Packet Filtering Firewalls or PFFs work by. These security measures are available as intrusion detection systems. Intrusion Detection System will scan all incoming and outbound network activities and will identify suspicious patters that may be the indication of someone trying to gain access into a computer system.
Knowledge based intrusion detection systems are far more common they work much like anti-virus software. This means the IDS will respond to the attack and take actions to block the malicious activity. Highlights in hybrid learning.
Intrusion Detection system It identifies intrusions by certain pattens that hackers would use when trying to penetrate the network. Knowledge based only does what youre asking to do and there are hundreds. M1 - Explain The Operation Of Different Intruder Detection Systems.
Active intruder detection systems are able to detect malicious activity and counteract this activity. Networked Systems Security P1 P2 M1 P1 describe how networks can be attacked P2 describe how networked systems can be protected M1 explain the operation of different intruder detection systems. M1- The Operation of Different Intruder Detection Systems The Operations of Different Intruder Systems Firewalls limit the data that can pass through them It also protects a networked server or client machines from damage by any authorised users.
Active Passive IDS. Intrusion prevention is the process of performing intrusion detection and then stopping the detected incidents. M1- Explain The Operation of Different Intruder Detection Systems F irewalls And V irus Protection- these two applications are fundamentally different the.
Describe how networked systems can be protected. Explain the operation of different intrusion detection systems M1 NIDS Intrusion detection systems are important if you want to keep your network secure. The biggest advantage of this is.
A Firewall is a software or hardware-based network security system that controlsmonitors the incoming and ooutgoing network traffic by analizing the data packets and determing wehther they should be allowed through or not based on an applied rule set. Operation of different intruder detection systems. Operation of different intruder detection systems M1 Explain the operation of different intruder detection systems Active and Passive IDS.
Firewalls Firewalls are designed to prevent unauthorised access to a computer or network. Discuss recent network threats. A firewall will monitor data packets coming in and out of the network it is protecting and will.
Passive intruder detection systems are only able to. M1 - Explain The Operation Of Different Intruder Detection Systems Firewalls Firewalls are designed to prevent unauthorised access to a computer or network. For example NIDS Network Intrusion Detection Systems this is a type of security that involves the placement along a strategic part of a network.
Network based IDS works by getting the individual packets that are passing through the network and checks each of them for the data it can get information and recognise data that is malicious that the firewall rules could not. NIDS systems monitor all of the traffic that passes through. M1 - Explain the operation of different intruder detection systems.
For example NIDS Network Intrusion Detection Systems this is a type of security that involves the placement along a strategic part of a network. Knowledge based intrusion detection systems are far more common they work much like anti-virus software. Intrusion Detection System IDS Intrusion Detection System is used to detect unauthorised entries and alert the administrator to respond.
Intrusion Detection System will scan all incoming and outbound network activities and will identify suspicious patters that may be the indication of someone trying to gain access into a computer system. A Passive system is a monitor and analyse network traffic activity that alerts an operator to potential vulnerabilities on the server. That it has a very low false alarm rate.

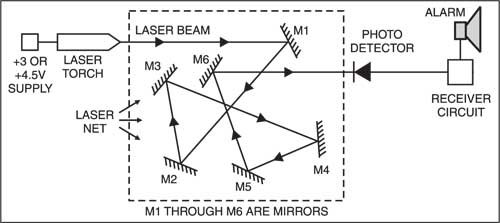
Intruder Detector Using Laser Torch Full Project Available
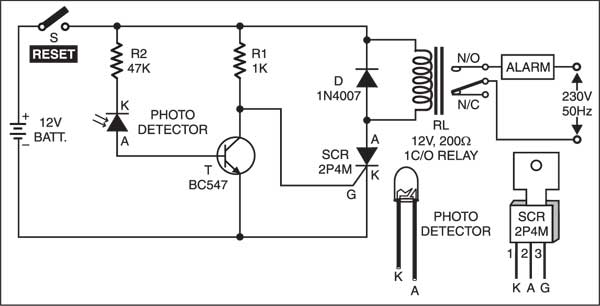
Intruder Detector Using Laser Torch Full Project Available
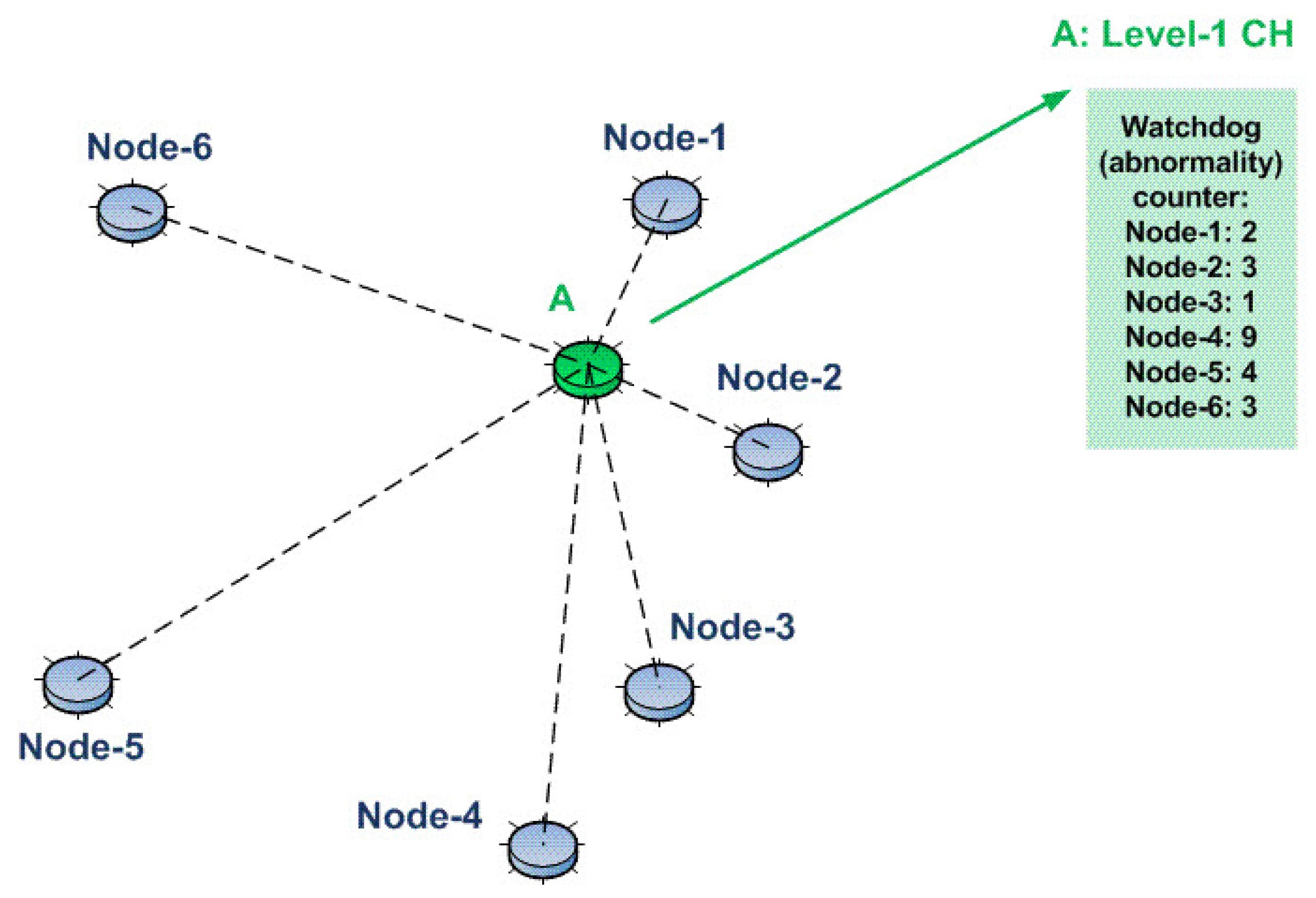
Sensors Free Full Text An Intrusion Detection System Based On Multi Level Clustering For Hierarchical Wireless Sensor Networks Html
Comments
Post a Comment